Now, API Shield automatically searches for and highlights Broken Object Level Authorization (BOLA) attacks on managed API endpoints. API Shield will highlight both BOLA enumeration attacks and BOLA pollution attacks, telling you what was attacked, by who, and for how long.
You can find these attacks three different ways: Security Overview, Endpoint details, or Security Analytics. If these attacks are not found on your managed API endpoints, there will not be an overview card or security analytics suspicious activity card.

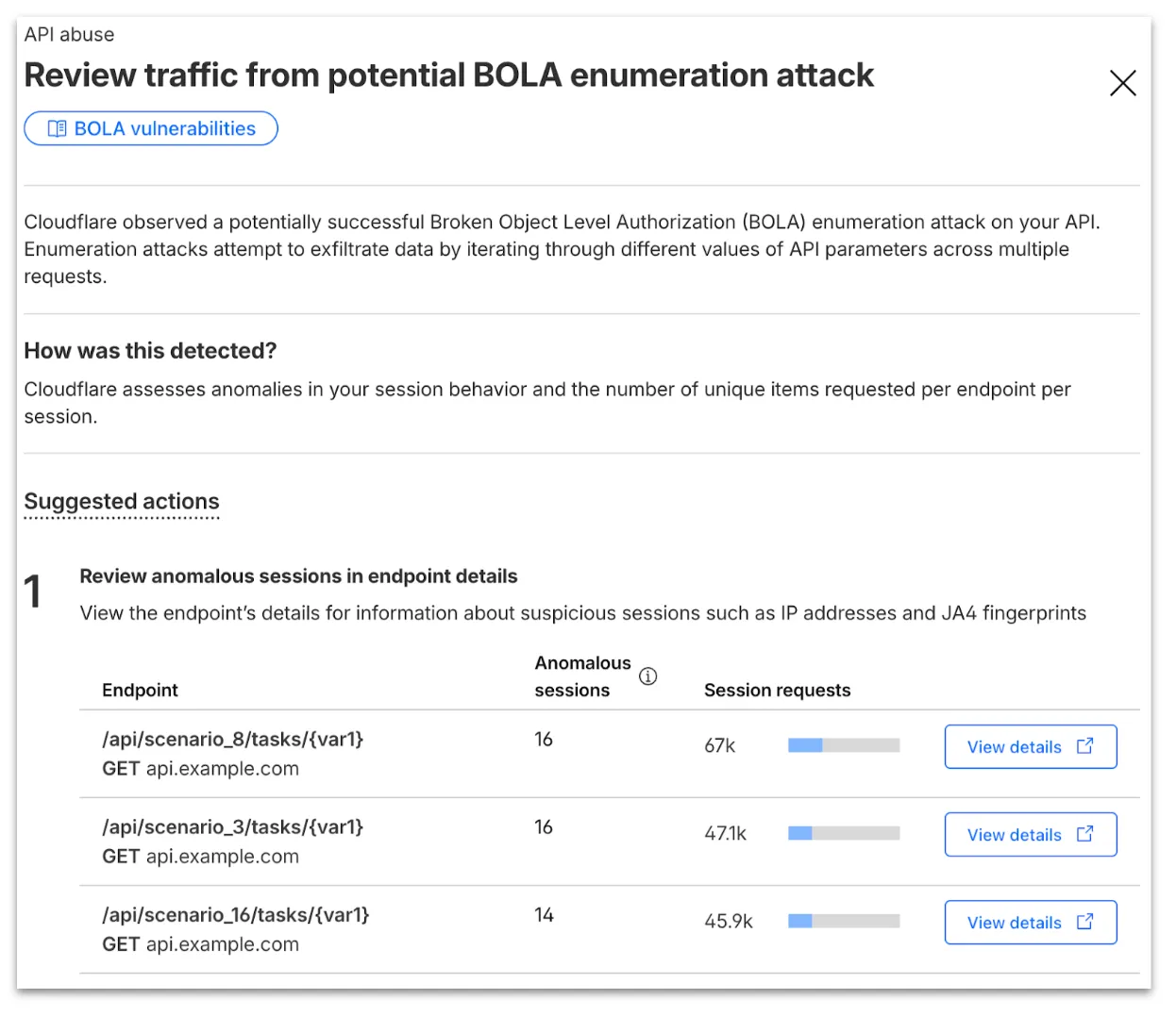
From the endpoint details, you can select View attack to find details about the BOLA attacker’s sessions.
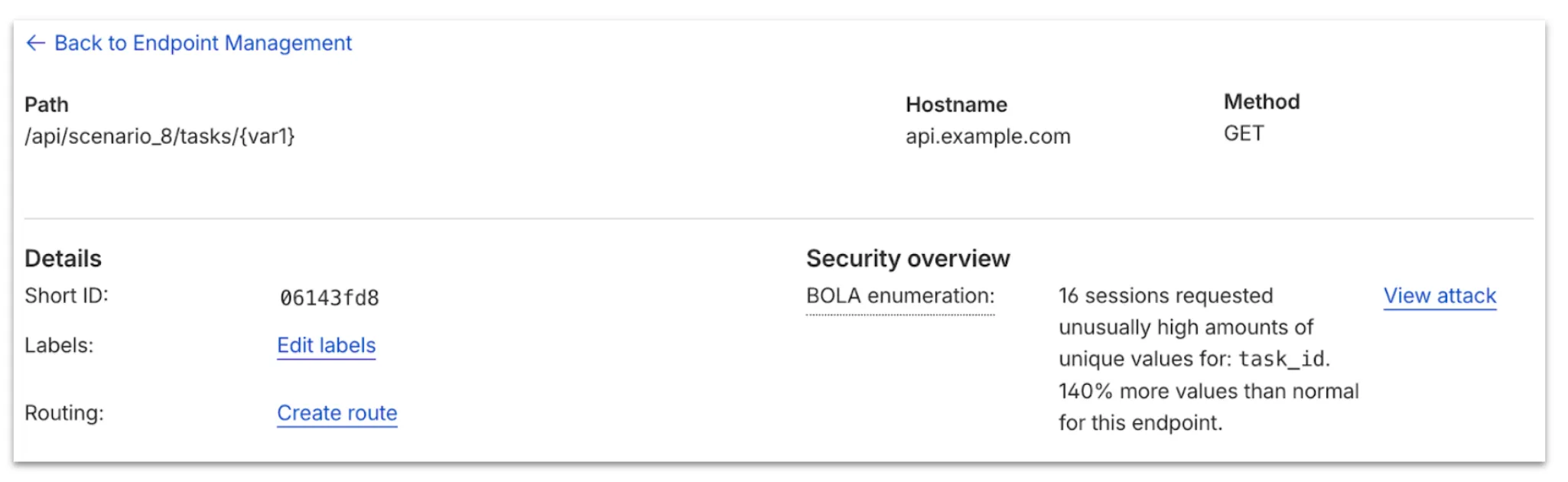
From here, select View in Analytics to observe attacker traffic over time for the last seven days.
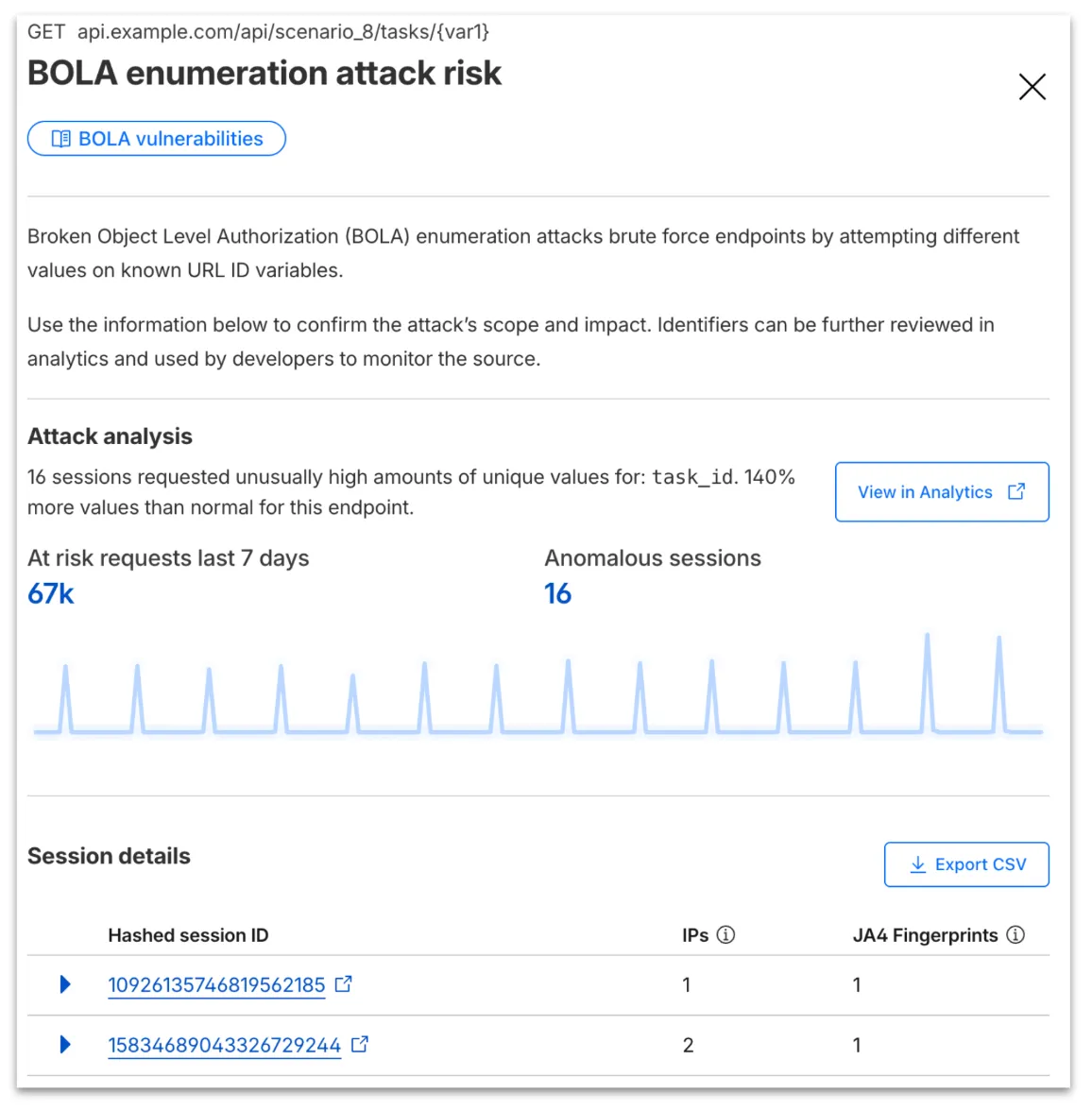
Your search will filter to traffic on that endpoint in the last seven days, along with the malicious session IDs found in the attack. Session IDs are hashed for privacy and will not be found in your origin logs. Refer to IP and JA4 fingerprint to cross-reference behavior at the origin.
At any time, you can also start your investigation into attack traffic from Security Analytics by selecting the suspicious activity card.

We urge you to take all of this client information to your developer team to research the attacker behavior and ensure any broken authorization policies in your API are fixed at the source in your application, preventing further abuse.
In addition, this release marks the end of the beta period for these scans. All Enterprise customers with API Shield subscriptions will see these new attacks if found on their zone.
Source: Cloudflare
Latest Posts
- Microsoft Entra ID: Auto-enabling passkey profiles [MC1221452]
![Microsoft Entra ID: Auto-enabling passkey profiles [MC1221452] 2 pexels magda ehlers pexels 613431](data:image/svg+xml;base64,PHN2ZyB3aWR0aD0iMSIgaGVpZ2h0PSIxIiB4bWxucz0iaHR0cDovL3d3dy53My5vcmcvMjAwMC9zdmciPjwvc3ZnPg==)
- (Updated) PowerPoint adds AI-powered image editing with “Designer editor” [MC1187787]
![(Updated) PowerPoint adds AI-powered image editing with "Designer editor" [MC1187787] 3 pexels tomfisk 3482724](data:image/svg+xml;base64,PHN2ZyB3aWR0aD0iMSIgaGVpZ2h0PSIxIiB4bWxucz0iaHR0cDovL3d3dy53My5vcmcvMjAwMC9zdmciPjwvc3ZnPg==)
- New policy to add watermarks to content generated or altered by using AI in Microsoft 365 [MC1221451]
![New policy to add watermarks to content generated or altered by using AI in Microsoft 365 [MC1221451] 4 pexels merlin 11137997](data:image/svg+xml;base64,PHN2ZyB3aWR0aD0iMSIgaGVpZ2h0PSIxIiB4bWxucz0iaHR0cDovL3d3dy53My5vcmcvMjAwMC9zdmciPjwvc3ZnPg==)
- Now available: 48xlarge and metal-48xl sizes for EBS optimized Amazon EC2 instances


![Microsoft Entra ID: Auto-enabling passkey profiles [MC1221452] 2 pexels magda ehlers pexels 613431](https://mwpro.co.uk/wp-content/uploads/2024/08/pexels-magda-ehlers-pexels-613431-150x150.webp)
![(Updated) PowerPoint adds AI-powered image editing with "Designer editor" [MC1187787] 3 pexels tomfisk 3482724](https://mwpro.co.uk/wp-content/uploads/2025/06/pexels-tomfisk-3482724-150x150.webp)
![New policy to add watermarks to content generated or altered by using AI in Microsoft 365 [MC1221451] 4 pexels merlin 11137997](https://mwpro.co.uk/wp-content/uploads/2025/06/pexels-merlin-11137997-150x150.webp)

![(Updated) Microsoft Viva: Viva Glint – New permissions [MC1217642] 11 (Updated) Microsoft Viva: Viva Glint – New permissions [MC1217642]](https://mwpro.co.uk/wp-content/uploads/2025/06/pexels-cottonbro-5474294-96x96.webp)
